Cybersecurity Simplified for the Insurance Agents
What is the NAIC Insurance Data Security Model Law 668?
In recent years many data breaches involving large insurers have shaken the industry. As a result, the National Association of Insurance Commissioners, partnering with state regulators, worked to create a uniform set of cybersecurity standards, becoming the Insurance Data Security Model Law in 2017. Since 2017, multiple states have adopted this law, while others, like New York, have used this as a basis for their own guidelines.
State Adoption Status of Model Law 668
In the coming years the law will be mandated for all states
What does the NAIC law require?
6 Core Requirements
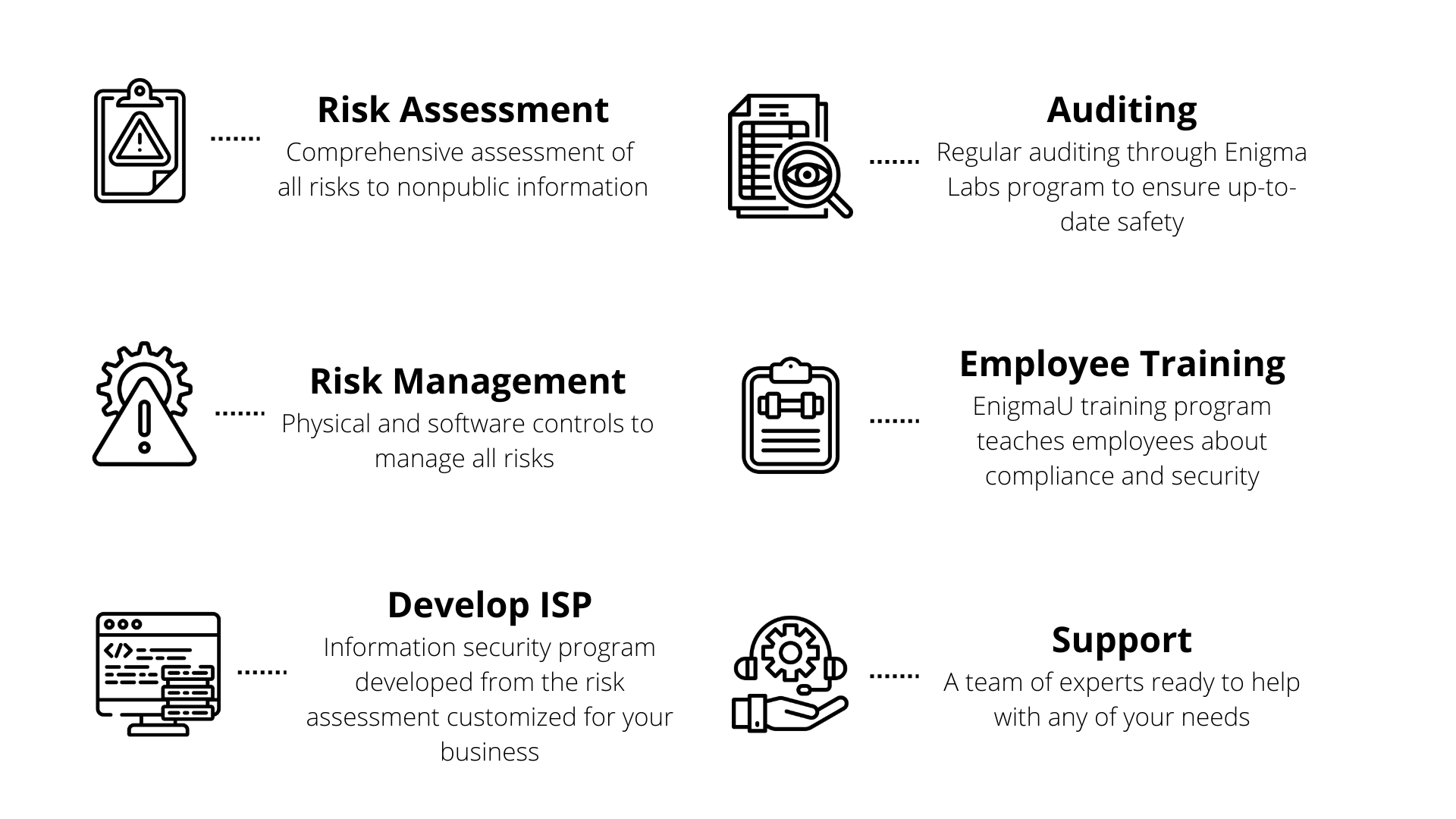
Creating and maintaining an Information Security Program
Performing continuous Risk Assessments
Creating and following a Risk Management Plan
Annual reporting for board oversight
Implementing 3rd party tools and services
Creating an Incident Response Plan
Information is taken from NAIC
Enigma Checklist
Prepare for Compliance with Enigma
-
As a third party service provider, Enigma offers the ability to become compliant and stay compliant.
Enigma offers a comprehensive security platform composed of all the cybersecurity resources and training material required for your agency to become compliant and secure.
-
Here at Enigma, we will help you assess risks and develop an information security program. We also create a tailored incident response plan for your agency in case a cybersecurity event occurs and we need to respond.
All of this is done through our easy to use Enigma Platform.
As part of this program, Enigma can help you to implement the required security tools and procedures, configure access controls, and create and manage your cybersecurity policies.
-
Train your employees through our unique program, EnigmaU, to ensure staff is up to date on the latest cybersecurity risks, vulnerabilities and phishing trends.
So they don’t fall victim to phishing and social engineering attacks that could compromise your (and your customers) sensitive data.